Why creating a WiFi network for guests is a good idea (and how to create one)
Table of Contents

In the hyperconnected world we live in, we don’t think too much about asking for or sharing the WiFi password when visiting a friend’s house, going to a company’s offices for a work meeting or having a coffee in a bar.
However, transferred to the physical world, it would be something like giving someone a copy of your keys: you are allowing them access to your home or business at any time, without supervision, and with access to all your privacy, sensitive information and valuable belongings.
By sharing your WiFi password, not only are you allowing other people to access the internet from your connection, but their devices are now connected to yours and can interact with each other and share, for example, malware or ransomware.
To avoid this vulnerability in the security of your local network, it is a good idea to create a guest WiFi network, which allows them to access the internet, but keeps them isolated from your local devices.
Risks of opening up your WiFi to visitors and customers
The more devices from outside your network that have access to your private network, the more vulnerable it becomes and the greater the risk of cyber attacks through devices over which you have no control.
Take, for example, a restaurant that offers free WiFi to its customers. This should be a guest WiFi network, to which only customer devices connect.
By sharing a network with your guests, you are opening the door to malware that they may have.
Under no circumstances should the same network be used to connect computers, POS terminals and other business devices so that they all share the same network. This means that anyone connected to the free WiFi could see the business devices and, in the worst case, launch an attack against them.
The risks are no less at home. If, for example, your best friend has a virus on their mobile phone without knowing it and connects to your home WiFi network, the malware can replicate and spread to all your networked devices, from the games console to the work laptop.
Advantages of the guest WiFi network
A guest WiFi network is a simple and effective way to protect the security of your network and your devices when you want to give visitors at home and in the office, or customers of your business, access to the internet.
The first major advantage of setting up a guest WiFi network is that devices connecting to this network are isolated in their own environment and do not have access to your local devices, data and services. So they can’t “sniff out” your private information or transmit computer viruses.

This can also be achieved with mechanisms such as Client Isolation, which means that each device connected to the WiFi is in its own bubble, preventing them from communicating with each other.
But the guest WiFi network has another great benefit: access control. The guest network has a separate password, so you can change it whenever you want without having to reconfigure access for all your local devices or leave them offline during that time. Plus, you have the peace of mind of knowing that no foreign device has “sneaked” into your home network.
In addition to separating your own and other devices, a guest network allows us to set filters or quotas
A third advantage is that, as it is a different network from the one you use at home or at work, it allows you to manage internet traffic separately for your guests. For example, you can limit the connection speed on the guest WiFi network with QoS, create traffic quotas or set filters and blacklist pages to limit the type of services that visitors can access.
How to create a secure guest WiFi network
Creating a guest network is simple and, in general, you can do it directly from your router. To configure a guest WiFi network on your router, follow these steps:
- Access the IP address of your router in the web browser. By default, it is usually 192.168.1.1 or 192.168.0.1.
- Log in with your administrator username and password. If you haven’t changed them, the manufacturer usually provides them on a sticker on the router and they are often as simple as admin, root, 1234.
- In the configuration menu, search for and activate a new WiFi network for guests (new SSID).
- Assign a name to the network, a password and an authentication method (WPA2 should be sufficient). By default, the router usually adds “guest” to the end of your main network name.
- Save the changes.
Once configured, the guest network does not require specific maintenance. It is important to carry out periodic checks to verify that the network is still configured correctly and separating the traffic from the corporate or home network. It is possible that certain changes, such as a firmware update or the activation of a new functionality, may affect its operation.
Specific instructions for companies
In companies, especially those with a high volume of uncontrolled access, it may be a good idea to create a WiFi network for guests with a new router or access point. It is slightly more complex, since in addition to the new SSID you must make sure that it is on a separate network (VLAN).
With these devices you can set up captive networks, like the ones used in many public spaces, such as airports or libraries. It is an open network, but when you connect to the internet you land on the registration page. Once you have obtained a username and password, you can browse.
If you are a user of one of these networks, it is advisable to use a VPN to encrypt internet traffic from your computer, tablet or smartphone. As they are open, we do not know how they manage our communications and if someone could be intercepting our data.
Common mistakes to avoid when setting up a guest WiFi network
Although creating a guest network is simple, there are some important details to keep in mind to ensure that it works properly and is secure for users.
These are the main mistakes to avoid when creating a guest WiFi network:
- Don’t leave the network open or with a weak password. The security of the secondary network is as important as that of the main one. If you leave it without a password or with an easy-to-crack one, you put both your secondary connection and the devices of your friends, family, partners and customers at risk.
- Choose WPA2 encryption or higher. Older encryption methods, such as WEP and WPA, do not offer much in the way of protection these days.
- Update the key regularly. Especially if you share your guest network with many users for short periods of time. Changing the password from time to time allows you to better control access and maintain the security of your secondary network if the previous key was compromised.
- Limit bandwidth. Keep in mind that, even if they are two different networks, they use the same internet connection. If you don’t limit the bandwidth of the secondary network, you may experience slow speeds or intermittence due to device saturation.
- Filter traffic and block malicious websites. A single access to a malicious site by one of your guests is enough to download malware that can infect the entire network and connected devices. And if someone visits illegal websites, remember that it is your IP that will appear in a potential police investigation.
- Monitor network usage. The guest WiFi network, although separate from your main network, is still part of your ecosystem. You want to have information about how much and how it is used to verify that it is secure, that it is working properly, that it is not weighing down your home or corporate network, and that no strange or illegal uses are being made from your IP.
How to monitor and control the use of a guest WiFi network
There are various tools you can use to monitor the use of any WiFi network, including guest networks. In general, the administration panel of any router allows you to see the connected devices and, depending on how sophisticated it is, it will provide you with more detailed information.
Another option for monitoring the guest WiFi network yourself is Acrylic Wi-Fi Analyzer. With this tool, you can see in real time the devices connected to your WiFi network or any other, even if you are not connected to the same network.
This way, you can see the number of connected clients and the inventoried devices with names, allowing you to identify possible devices that should not be connected and act accordingly.
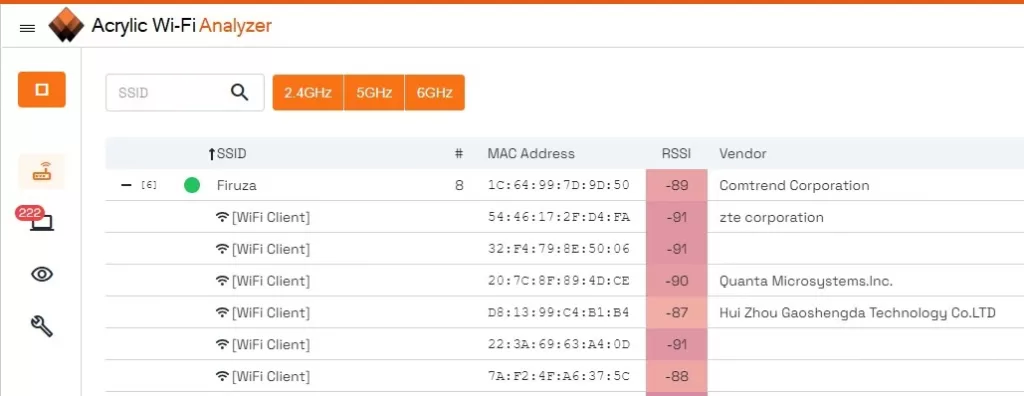
These are good options for individuals and small businesses that want to offer free and secure access to their visitors, while maintaining the security of their homes and businesses.
For more ambitious companies, tools such as NetAlertX can be interesting, allowing 24/7 monitoring of a network and viewing of connection data, etc. The disadvantage is that it requires the installation of dedicated computers and a greater knowledge of computing and networks to use it.
Solutions such as pfSense or OPNsense offer much more detailed control, allowing you to manage VLAN independent networks, set firewall rules and other functionalities. In this case, the installation must be carried out by a specialized company, as it requires complex deployments and configurations.